Nearly 38 million records containing personally identifiable information (PII) were inadvertently exposed through a misconfigured setting in a Microsoft tool this summer.
According to a report published at the end of August by UpGuard, an information security company that discovered the leak, 47 entities fell victim to a default configuration in Microsoft Power Apps that made their data sets findable by search engine or anyone with knowledge of the web address.
The data leak affected large entities such as American Airlines, Ford, and governmental bodies such as New York City, Maryland, and Indiana. Discovered in May, it divulged COVID-19 contact tracing efforts, vaccine registrations, and employee ID information such as home addresses and social security numbers.
Power Apps is a low-code development platform for creating business intelligence tools, making it easy for users to create their own web and mobile apps. UpGuard reported that while the Power App portal’s default settings secured data organized into tables, data sets that were organized as lists were left unprotected. In order to keep that information private, it had to be manually configured.
After UpGuard reported the configuration issue to Microsoft on June 24, the leaks were plugged and the ability to access the information was removed. There’s no indication as of yet that any of the exposed data has been compromised.
Also read: Data Governance Can Ease PII Regulation Compliance
Is Microsoft to blame for the leak?
This breach is just the latest example of how easily sensitive data can be exposed when it’s unclear how the complex software environment is designed. And of course, it’s also a shining example of the importance of double and triple checking that every potential cybersecurity hole is plugged.
Per UpGuard’s report:
The number of accounts exposing sensitive information…indicates that the risk of this feature…has not been adequately appreciated. On one hand, the product documentation accurately describes what happens if an app is configured in this way. On the other hand, empirical evidence suggests a warning in the technical documentation is not sufficient to avoid the serious consequences of misconfiguring OData list feeds for Power Apps portals.
Below is a screenshot of Microsoft’s Power Apps Portal’s documentation warning.
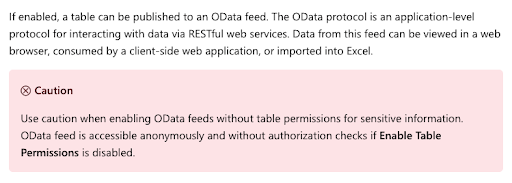
So yes, Microsoft did do its part in warning users
of the consequences, but the complex nature of the tool led to organizations either ignoring or not fully understanding the issue. When UpGuard first notified Microsoft of the issue, the tech giant contended that the “behavior is considered to be by design.”
Once news of the breach broke, Microsoft released a statement to Engadgetsaying, “Our products provide customers flexibility and privacy features to design scalable solutions that meet a wide variety of needs. We take security and privacy seriously, and we encourage our customers to use best practices when configuring products in ways that best meet their privacy needs.“
After Microsoft formally closed the case in late June, UpGuard (you read that right — not Microsoft) began notifying affected organizations, and many plugged the leak within days.
On August 22, Microsoft changed the default settings so that organizations using Power Apps’s basic templates and design tools will have the privacy setting enabled automatically.
This incident goes to show that no matter how small the issue may seem, developers should make sure to check their settings and heed warnings, especially when using an API they haven’t created themselves.

