More people are using smartphones for their work than ever before, and often, it’s their personal device. In fact, 75% of employees use their personal devices to access work resources. In this new age of bring your own device (BYOD), companies need to ensure employees’ devices are following the same security standards as the business’s devices. Enterprise mobility management (EMM) software keeps business resources secure while allowing employees to work on the go.
To skip the guide and get a personalized list of enterprise mobility management software recommendations, use our Product Selection Tool by filling out the form on the right side of this page. It’s free, and in as little as five minutes, you’ll get a list of tools that will meet your business needs.
Jump to:
- What is EMM Software?
- Compare the Best EMM Solutions
- Key Features of Enterprise Mobility Management Solutions
- Benefits of EMM Platforms
- Trends Affecting Enterprise Mobility Management
- Choosing the Best EMM Software for Your Business
What Is EMM Software?
Enterprise mobility management, or EMM, software is a type of business technology that secures company and employee-owned mobile devices using device policies, remote access, and application control.
EMM software includes mobile device management (MDM) and limits how applications can share corporate data, while still giving users full control over their personal apps and data. Using EMM, IT can manage a variety of devices and platforms — including iOS, Android, Windows, and Chrome OS — through a single console.
Compare the Best EMM Solutions

|
no | no | no | no |

|
yes | yes | no | yes |

|
yes | no | yes | no |

|
no | no | no | no |

|
yes | yes | yes | yes |

|
no | yes | no | yes |

|
yes | no | yes | no |

|
yes | yes | no | yes |
| Product | iOS & Android Support | Location Tracking | Phishing Protection | Kiosk Mode |
|---|
Addigy
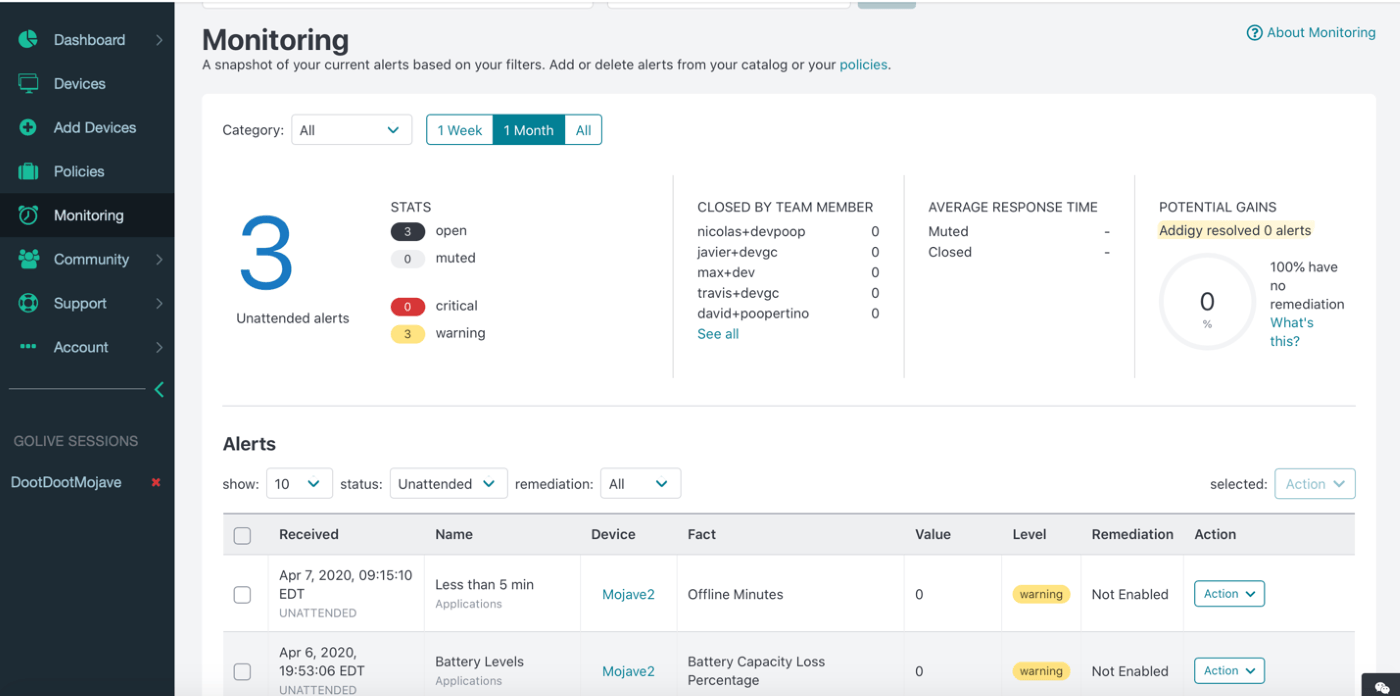
Addigy is an enterprise mobility management solution focused on macOS and iOS devices. Administrators can quickly identify devices connected to your network and investigate them to make sure they’re tied to authorized users. With remote support, employees can easily ask IT questions and get real-time answers, solving issues faster and improving productivity. Addigy also offers military-grade password encryption and MFA to keep devices and data secure.
Pros
- Enrollment is quick and easy
- Provides a lot of information about devices to IT
Cons
- UI is less user-friendly than other solutions
- Some updates require admin access to install
Hexnode UEM

Hexnode UEM offers a unified endpoint management solution that puts all devices that access business data into one centralized management console. Administrators can easily deploy enterprise applications, while simultaneously blacklisting dangerous apps to prevent them from getting access to company data.
For in-office users, Hexnode also allows IT to grant WiFi access to devices without giving out the password, ensuring only authorized devices can join the company’s network.
Pros
- Easy to learn with good documentation
- Simple, user-friendly design
Cons
- Platform doesn’t support Windows devices as well as Macs
- Blacklisting applications doesn’t always work
IBM MaaS360 With Watson
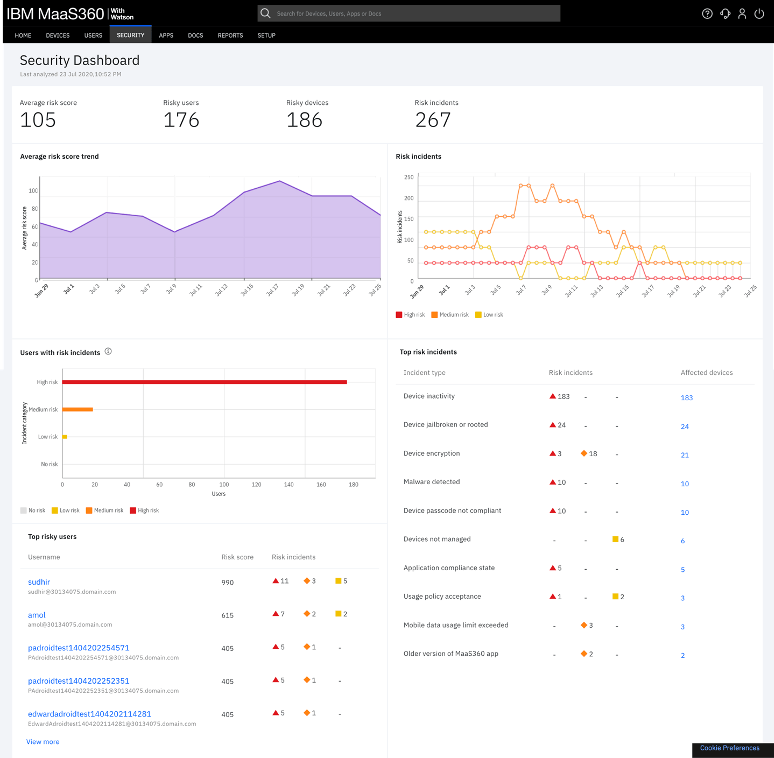
IBM MaaS360 with Watson is an AI-driven UEM solution to help you secure your employees’ mobile devices. AI and predictive analytics identify potential threats before they gain access to the network, allowing your IT team to investigate and shut them down if necessary.
The system can also automate parts of the remediation process, reducing the manual work your IT team has to do. The SaaS model makes it easy to scale as your company needs to add more devices.
Pros
- Very versatile and supports several operating systems
- Management console is easy to use
Cons
- Some users have experienced glitches during installation
- Customization is limited
Jamf Pro
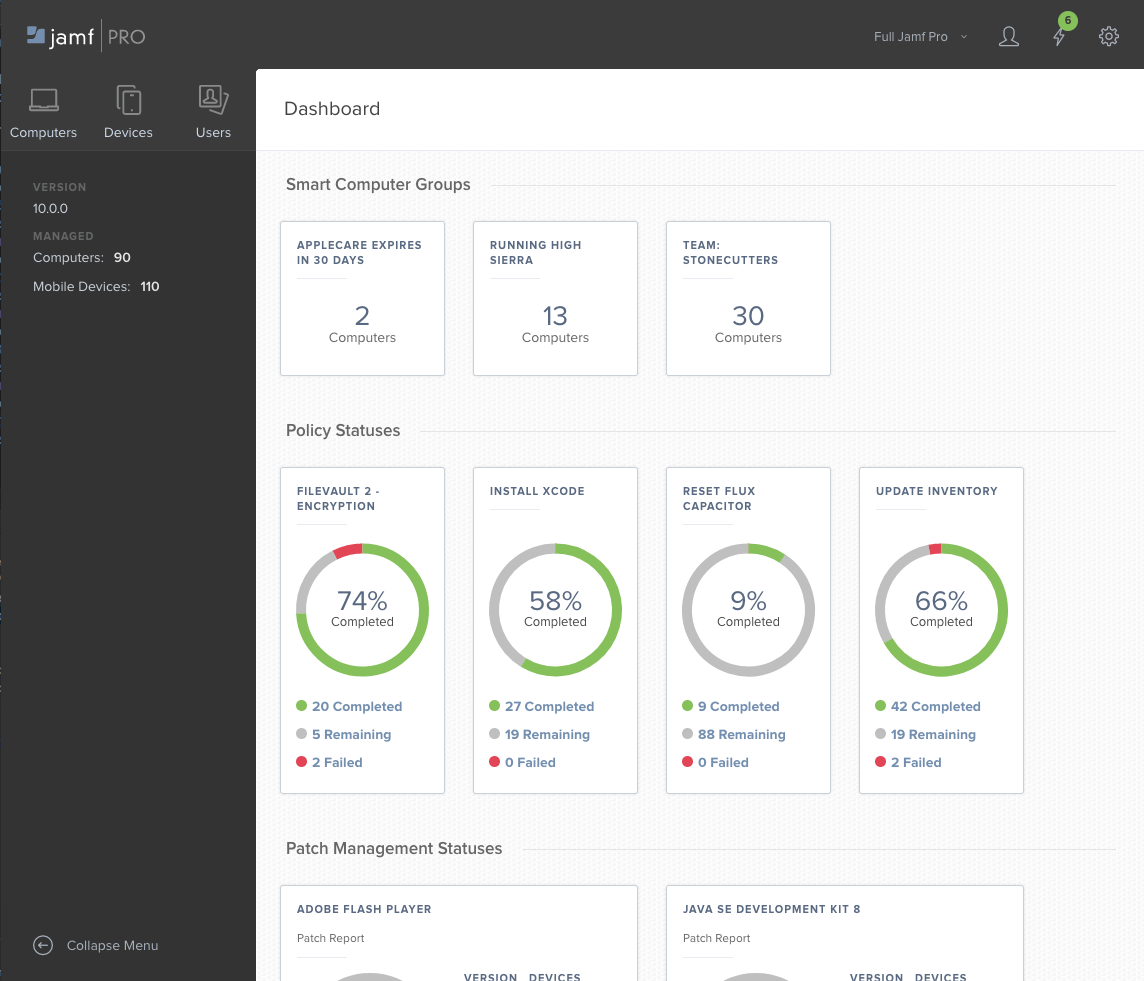
Jamf Pro (formerly Casper Suite) is EMM software that supports macOS and iOS devices with easy and secure remote deployment. You can purchase apps in bulk for your team and then distribute them as necessary.
Jamf Pro is available both on-premises and in the cloud, giving you complete control over your deployment. The dashboard shows IT which devices need to be updated, which users haven’t followed the recommended settings for email and other applications, and how many devices are connected to the network.
Pros
- Several avenues for support
- Admins can quickly view their current device inventory
Cons
- Some issues are only solvable with third-party solutions
- Learning curve can be steep, especially for more advanced features
ManageEngine Mobile Device Manager Plus

ManageEngine Mobile Device Manager Plus is mobile device management (MDM) software that supports Apple, Android, Windows, and Chrome devices. It’s easy to enroll and authenticate devices with the system, as users can enroll themselves, or you can bulk enroll devices with a CSV upload.
With remote access, IT can view devices in real time and troubleshoot issues to get them back to operating normally. And IT can also remotely wipe data from the device when employees leave or no longer need access to it.
Pros
- Easy to deploy and set up patching
- Helpful and responsive customer support
Cons
- Deployment can be slow and sometimes fails with no information on why
- Interface can be complicated and has a learning curve
Scalefusion
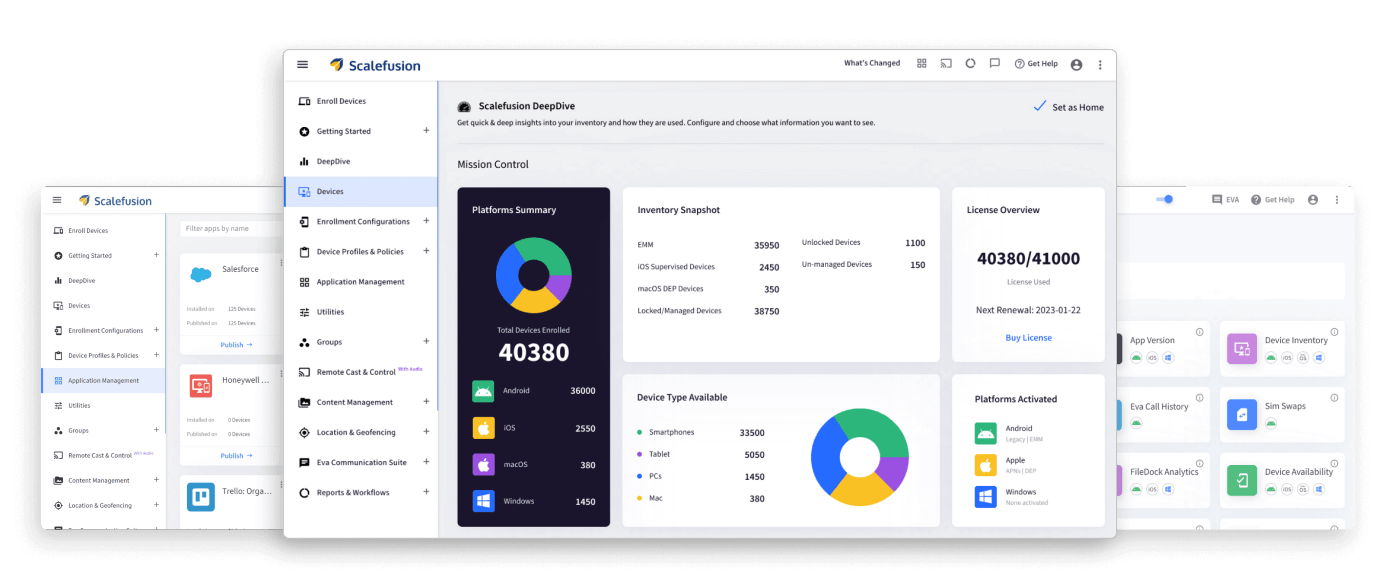
Scalefusion is EMM software that provides full visibility into the devices your employees use for work — including smartphones, tablets, and rugged devices like POS systems. It supports Windows, Android, and iOS devices and provides a clean dashboard, making it easy for IT to understand which devices are connected and how they’re being used.
The reports are customizable and easy to share. Scalefusion offers free live-chat support and managed services to keep your business data secure.
Pros
- Helpful and responsive support team
- Clean user interface and strong documentation
Cons
- Device enrollment can take a long time
- The remote support sessions have a slight lag
Sophos Mobile

Sophos Mobile is a secure UEM platform for Windows, Apple, and Android devices. The inventory and asset management features identify connected devices and provide detailed reports on device usage and necessary updates.
Employees can enroll their own devices in the system and reset their own passwords without involving IT. Sophos Secure Email also adds a secure container to employee devices to keep their business email separate from their personal email, providing an extra layer of protection.
Pros
- Provides a single console for managing all devices connected to the company network
- Remote factory reset protects data in the event of a lost or stolen device
Cons
- Android devices sometimes have update failures
- Windows support is lacking compared to iOS and Android support
VMware Workspace ONE
VMware Workspace ONE is an application and endpoint management solution that allows you to monitor and manage endpoints from a centralized console. It’s available both on-premises and in the cloud. It also includes zero-trust security protocols to verify each user’s identity before they gain access to company data.
VMware Workspace ONE automates common IT tasks like patch management to reduce IT’s manual workload and improve efficiency. And the machine learning features provide actionable insights to help you fortify against vulnerabilities.
Pros
- Corporate data is stored in separate containers from personal data
- Administrators can block device enrollment
Cons
- On-premises deployment can be complex and require additional hardware
- Integration with other security tools can be difficult
Key Features of Enterprise Mobility Solutions
When looking at EMM platforms, you should make sure the tools you’re considering include at least the following features.
Behavioral Analytics
Using artificial intelligence (AI), EMM software can analyze a user’s behavior and identify anomalies that might signify a lost, stolen, or hacked device.
For example, if an employee typically works from 9 a.m. to 5 p.m. but strangely logs into a corporate application at 2 a.m. one day, the EMM solution can block access and send an alert to IT, so they can investigate. Humans are creatures of habit, and they typically access applications around the same time or in the same order, which can let EMM solutions identify other users faster.
Zero-Trust Security
EMM solutions should be able to assign user permissions to each device, only allowing them access to the applications and information users need to do their job. Additionally, it should turn on identity and access controls for company applications, using either multifactor authentication (MFA) or biometric data before letting users in.
Zero-trust security relies on users verifying their identity each time they want to access corporate data, preventing a bad actor from getting access by stealing or hacking a device.
Also read: 3 Steps to Implementing Zero Trust in a Sustainable Way
Scalability
As businesses grow, they need a solution that can grow with them. EMM tools should include a tiered pricing model that allows you to start small with only the features you need and expand as you need more functionality.
Additionally, subscription models based on the number of users or devices help businesses scale platforms as needed, rather than having to jump up to the next tier just because they exceeded the device limit.
Remote Installation and Device Control
With the rise in remote work, it’s unlikely IT is going to be installing the EMM solution on each device in the office. Instead, they’ll need to implement the tool remotely and get access to each device wherever it is. IT can create policies and push them out to each device, while also being available for remote users that need device support.
Benefits of EMM Platforms
EMM software provides better security for businesses that allow remote work through standardized policies and data control.
Policy Standardization
Companies can already implement security policies on their in-house and owned devices, but employee-owned devices used to present a large hole in an organization’s security framework. Thanks to EMM though, IT can now implement the same policies on both static and mobile devices to close vulnerabilities in the network.
Improved Security Analytics
With security tools in place on mobile devices, companies can now see how employee mobile devices affect their overall security. EMM software includes reporting and analytics that can tell organizations how many potential issues come through mobile devices and where any major vulnerabilities lie — including which applications see the most breach attempts.
Lower Technology Costs
When companies allow employees to use their own devices for work and still keep them secure, they don’t have to spend as much to provide devices to employees. EMM software typically costs only a few dollars per user or device, depending on the included features.
In contrast, a new smartphone could be anywhere from $200 to $1500. Plus, some employees like to work from tablets due to the bigger screen, which would add another expense if companies had to provide them.
Trends Affecting Enterprise Mobility Management
EMM is gaining popularity thanks to a few different trends.
Remote Work
In the midst of COVID-19, many companies shifted their employees to working remotely, allowing the business to continue to run without workers onsite. However, many of these businesses didn’t have the overhead to provide new devices to their employees.
Many organizations turned to EMM software to provide a secure way for employees to access company data and applications. And as remote work becomes the new norm, organizations will continue to need enterprise mobility management tools to protect their data.
Rise in Ransomware
Several high-profile ransomware cases over the past few months have pushed cybersecurity directly into the public eye. Consumers and companies alike need more information on who has access to their data and what is protecting it. With the analytics from EMM software, organizations can get a better idea of their vulnerabilities and provide more protection for themselves, their employees, and their customers.
BYOD Policies
Rather than purchasing company-owned smartphones for employees, businesses are now allowing their workers to access company information from their personal devices. Employees likely already know how to use these devices, so they’re easier to get up and running, and people are likely to take better care of devices they purchased themselves.
While BYOD is cheaper than buying new devices, it opens organizations up to potential attacks, making EMM software a necessity.
Choosing the Best EMM Software for Your Business
When choosing enterprise mobility management software for your business, opt for a solution that helps you identify potential breaches and vulnerabilities quickly. These services should have the scalability you need to continue using the platform as your business grows.
Consider starting with a small group of devices to try out a solution before undertaking a full-scale deployment. This way, you’ll get a better idea of which features you do and don’t need, and understand how well the platform works for your business.
If you’re still not sure which solution is right for your business, use our Product Selection Tool on the right side of this page. After answering a few questions, you’ll get a personalized list of EMM software recommendations tailored to your business needs.
Read next: Digital Transformation Strategy & Guide 2022